Usable Privacy and Security
Modern society depends on computer systems being highly reliable. However, in recent years, we have seen a growing number of severe privacy and security failures due to human factors issues, including: hard-to-use interfaces, incorrect mental models, and the overall burden of high security.
The goal of Usable Privacy and Security is to make these systems more reliable in practice by designing, building, and evaluating systems that consider the human element, drawing on ideas from cognitive psychology, social psychology, interaction design, and more. We work closely with campus-wide initiatives such as CyLab in designing for and studying privacy and security.
Students who want to learn more about this HCI research area might be interested in the following HCII courses:
Faculty Researchers
-

CMU at CSCW 2025
NEWSCarnegie Mellon University authors contributed to 27 papers accepted to the 2025 ACM Conference on Computer-Supported Cooperative Work and...
-

Protecting Audio Privacy at the Source
NEWSSound is a powerful source of information. By training algorithms to identify distinct sound signatures, sound can reveal what a person is...
-

CMU at CHI 2024
NEWSResearchers from the Human-Computer Interaction Institute (HCII) and several other Carnegie Mellon University schools and disciplines cont...
-
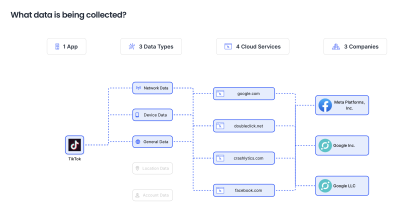
New website highlights thousands of Android apps’ data collection practices
NEWSResearchers at Carnegie Mellon University have launched a new website, offering Android users an easy and convenient way to see how their ...
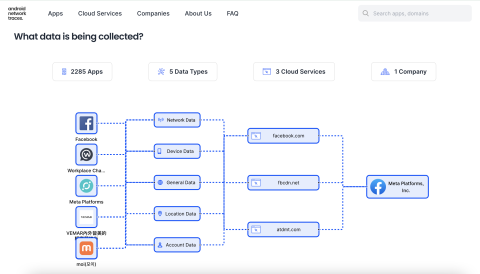
Android Network Traces
PROJECTSmartphone apps collect and send a great deal of data about us to third-party websites, but what are they collecting and where are they sending it?...
-
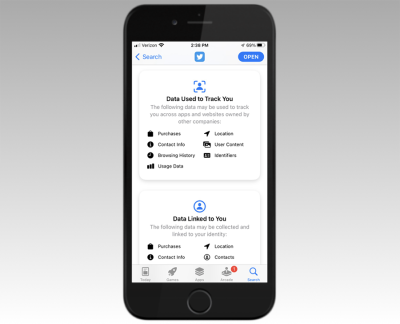
CyLab Researchers Investigate Apple's Privacy Labels
NEWSCyLab researchers will present two papers at the upcoming ACM CHI Conference on Human Factors in Computing Systems that examine Apple's pr...
-

SMASH Lab Uses Wearables To Train New Privacy-Preserving Sensors
NEWSData about home sales likely won't help someone looking for a car, just like information about basketball won't help someone playing baseb...
-
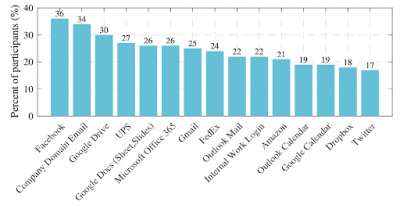
Account sharing sheds light on social cybersecurity
NEWSVisit the original blog post on the Center for Informed Democracy & Social - cybersecurity (IDeaS) website.
Social Cybersecurity
PROJECTOur research into the human factors of cybersecurity focuses on people as social actors whose security behaviors are influenced by their relationships, co...

